- Published on
How APCON network tools support the MITRE ATT&CK Framework
MITRE ATT&CK Background
When we think of the MITRE ATT&CK framework, we think of different security products that analyze the data to identify, isolate, and mitigate threats in your environment from external and internal threats. These threats are broken down into several categories and identify what tactics, techniques, and procedures can be used by the attacker to gain entry, move laterally to the system they wish to exploit, and exfiltrate the data they seek. When companies follow the MITRE framework, they strategically build their security posture to mitigate and stop the adversary from successfully exfiltrating the data from their environment.
However, there is indirect technology that assists the security products in receiving the data and analyzing it. This indirect technology is provided by APCON, offering a way for companies to cost-effectively collect traffic on the network to help various security products identify threats so you can mitigate any exfiltration or potential ransomware attacks. Due to the high cost of implementation, APCON has helped to manage the high cost of protecting data, intellectual property, and reputations from being destroyed so companies can successfully protect themselves. The ROI is significant as distributed security product rollouts would cost many millions of dollars.
APCON also has a product that both collects packets and acts as a server which allows different security companies to run their agents on our system. We collect the traffic off the wire, and the agent receives this traffic and either analyzes it or repackages it and sends it to their tool for analysis. It is a great way to avoid additional rack space and an increase in power costs in locations where space and power are at a premium.
APCON also offers Inline Bypass TAPs that do NOT directly put any of these tools inline. Rather, they provide a safe inline TAP for the network side to feed traffic to security tools (like IPS that tends to be inline) and then mirrors that traffic to other tools that also need to examine that data out of band. If the IPS tool goes offline, APCON automatically bypasses the tool and allows traffic to continue. We can allow for manual intervention as well.
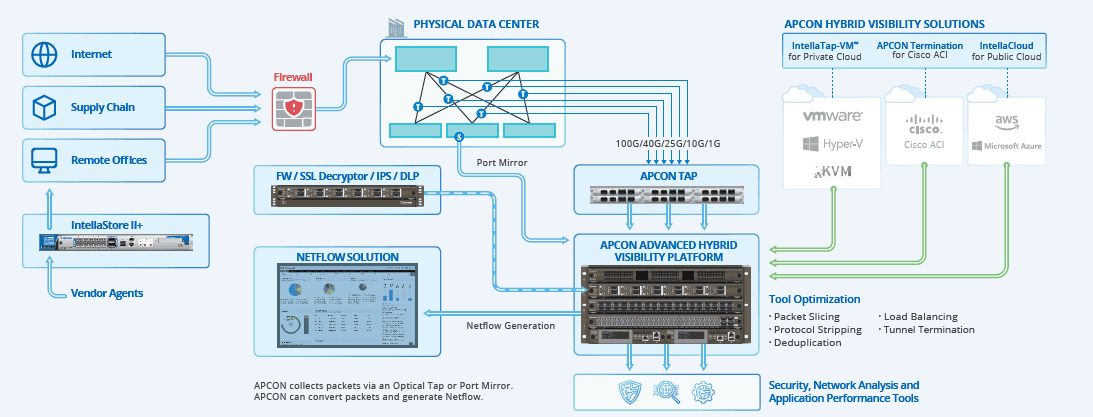
APCON also works with companies that provide decryption capabilities that may also sit inline so that you can decrypt the traffic out of band and send that traffic to the security products unencrypted for analysis. See the diagram below for an example of APCON deployment.
The APCON architecture shown in the diagram below depicts a centralized model of collecting traffic from anywhere, optimizing the packets, and sending them to the tools or generating NetFlow and sending it to the collectors.
APCON indirectly maps to the use of various security products in these areas
Reconnaissance
Adversaries tend to be strategic in that they want to learn about your environment before the attack. If an attacker is scanning for external-facing IP Addresses, you can collect these packets from your DMZ out of band and send them to a security tool that may be baselining and tracking bad IP reputations from threat intelligence sources. In this way, you can get ahead of a potential attack.
Resource Development
In this stage, an attacker could establish a connection with a mobile user or supply chain provider and learn about the network via a VPN connection. They can gain information about the infrastructure, accounts, or services just from watching what is traveling across the network. APCON can collect the VPN or supply chain connection traffic and send the packets to the security products that are able to analyze them for nefarious activities that would not be normal for that user or supply chain activity.
Initial Access
Initial access can be attempted by an internal or external adversary. If we are dealing with an external threat, adversaries are looking to penetrate your perimeter in a variety of different ways. If you collect traffic at the point of entry by tapping your firewall links or DMZ, you can feed APCON out of band packets that can reveal a payload used to deliver the malware after they have exploited a vulnerability in a system. APCON collects whole packets which contain the rootkit executables used to install backdoors and Command & Control functionality. When a hacker is successful in exploiting a system, there are no log files to work with, so packets become critical to providing the visibility needed to identify and isolate a threat. This also includes disgruntled internal employees executing vulnerability attacks on systems and looking to exfiltrate data from the company.
Execution
During a Command & Control session or a compromised VPN session, packets flow from the compromised system(s) to the external system used to gain entry. These packets provide a means to understand what HTML file, API script, or WMI function was used during that session. Adversaries do everything they can to hide what they are doing, but they cannot hide the packets flowing through your network. If APCON is deployed to collect the traffic in your network, you will have a chance to identify these patterns and mitigate the attack via your security solutions.
Persistence
External remote services like VNC, Remote Desktop Protocol, LogToMe, or Redundant Access like VPNs, C&C, or Port Knocking are ways that attackers maintain persistence. APCON can capture these packets and feed them to a security product that can analyze this traffic for suspicious TCP flags used, ports not commonly open for service, or other forms of persistent activity.
Credential Access & Privilege Escalation
One of the keys to a successful hack is the attacker’s ability to elevate privileges on a system. Once hackers have the highest privilege available, they can do anything they want on that system. APCON can collect packets off the wire so when a brute force attack occurs, the packets show a consistent attempt to connect to the system. Log files will show the consistent attempts and the packets will provide more details (i.e., the hacker is using an SSH connection to deliver a brute force script).
Defense Evasion
Many adversaries work diligently to avoid detection when sending traffic over the wire by encrypting data or packaging it in a commonly-used protocol like HTTP and DNS. APCON can provide the packets with that data to a security product to analyze and identify characteristics within the protocol or payload delivery in base64 which may not be common for that protocol and indicative of nefarious activity.
Discovery
Attackers who have control of a system with elevated privileges can run any tool or application. If they are seeking to identify systems by IP, hostnames, or other logical identifiers on the network to find their main objective, APCON can collect that traffic and feed that data to the security product able to identify this attempt and mitigate it.
Lateral Movement
More companies are segmenting their networks and baselining daily activities so they can identify potential lateral movement. APCON provides a cost-effective way to collect all traffic on the wire with the ability to forward this traffic to a variety of different security products that identify and contain lateral movement. This is a critical step in the attack lifecycle, so having the packets and the right security tool to examine these packets will be key in preventing successful lateral movement to your data. Some security products collect NetFlow to map a user’s activity on the network to identify whether that user is doing something nefarious. APCON can collect and transform packet data to NetFlow records and feed the security tools that only need NetFlow records.
Command & Control (C&C)
C&C usually involves an attacker who uses a compromised computer on the internet to control a computer system in your network to be able to slowly go through the process of exfiltrating the data they want. Different methods are used for C&C, but one of the most important ways to get visibility into this type of traffic is collecting whole packets. APCON will collect those packets off the wire and provide the security appliance with the right data. You can then implement a potential sinkhole of the connection to stop the attacker from using C&C successfully.
Collection
Attackers use common protocols to stage or collect data and put it on the host system they are using to exfiltrate data. One example is a user connecting to a SQL Database and moving that data to their system. When using baseline monitoring, this may indicate an unusual activity. APCON can collect this traffic and provide the full packet with payload allowing the security product you are using to know what is being copied to that host system. Having this type of visibility will allow you to mitigate the exfiltration of data.
Exfiltration
At this stage, when the attacker has successfully avoided all the protective steps above and has not been detected, they are now ready to exfiltrate data out of your environment. Various security products are used to detect and stop exfiltration like DLP and IDS/IPS systems. Since these products monitor for this type of traffic running over your network, APCON is there to collect the whole packet for all sessions so these security products can analyze for exfiltration and stop it.
Integrate Network Security Solutions with APCON
- Intrusion Detection Systems
- Intrusion Prevention Systems
- Data Loss Protection
- Incident Response and Detection
- Network Detection and Response
- SIEM tools that convert packets to logs
- Forensic solutions that conduct Security Orchestration, Automation, and Response
Concluding Statement
In reviewing the different parts of the MITRE Framework, APCON can provide various security products the packets necessary out of band as well as inline that allows those tools to analyze, identify, isolate and mitigate an adversary success in exfiltrating the data from your environment. The cost to an organization that has suffered an attack is enormous with a good reputation being the most difficult value proposition to recover from customers. Ensuring your security posture is effective means collecting packets off the wire, but that capability cannot break the bank. APCON can collect packets from physical and virtual environments with low cost to the business, therefore allowing successful rollout of your security architecture.